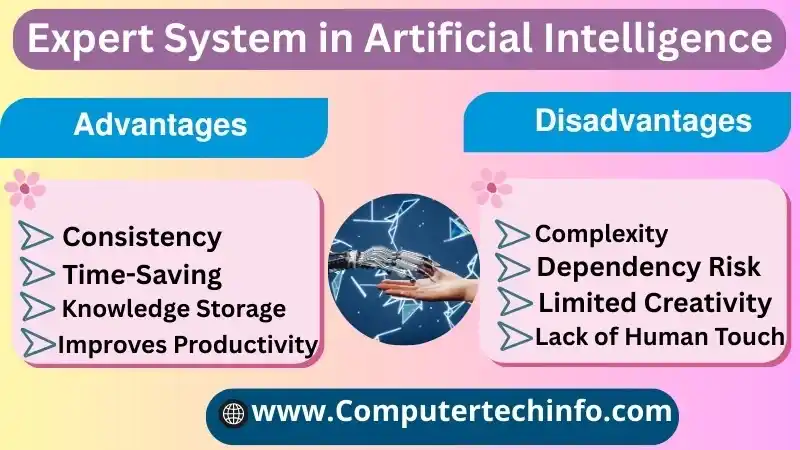
All types of firewall allow computer security system that monitors and controls network traffic. It is a software or hardware unit that blocks harmful traffic and allows only secure data packets, according to specific security rules.
A firewall is often visualized as a line that sits between the public internet and your device or network. It protects your network from various online threats. A firewall is a fundamental tool for network security that is constantly changing and adapting to all situations.

In this article, we’ll cover what a firewall is, various types of firewalls, how they differ from VPNs, how they work, and tips for choosing the right firewall that will be useful for your cyber security needs.
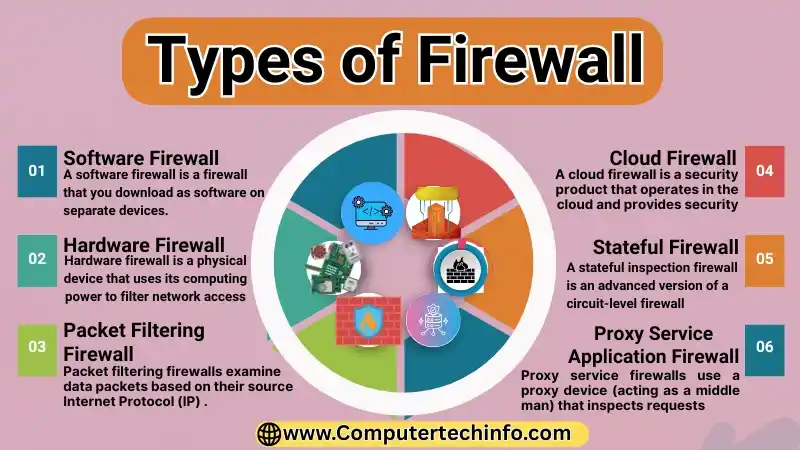
Types of Firewall with Diagram
Here are a more important firewall types for you to reviews:
Software Firewall
A software firewall is a firewall that you download as software on separate devices. It contains custom rules that help filter network traffic. A software firewall can allow one software or feature and block another, depending on whether it works with others or not use.
This type of firewall is very useful when you want to protect a single device from cyber (meaning anything connected to the internet) attacks. However, it requires separate setup and management for each device.
Not all devices are compatible (meaning they work properly) with the same software firewall, so it may sometimes be necessary to install additional firewall.
Hardware Firewall
A hardware firewall is a physical device that uses its computing power to filter network access. It can protect multiple devices connected to a single network, making it easy to install and useful for long networks.
Hardware firewalls protect devices by filtering network traffic that occurs between individual parts of the network. However, they do not protect against insider attacks, which occur when an internal employee or contractor uses this network without permission.
Packet Filtering Firewall
These rules include properties such as source/destination IP addresses, port numbers, and protocols.
Packet filtering firewalls examine data packets based on their source Internet Protocol (IP) address and the IP address. And, compare them against the rules set by the network manager.
This firewall monitors each packet individually without tracking whether the connection is already open. This limits its capacity. This means it that cannot detect or prevent application-layer attacks.
Internet security personnel typically use this type of firewall to protect networks from malware (malicious software) and harmful applications.
Circuit-Level Gateway
Circuit-level gateways are a simple type of firewall designed to quickly approve or deny traffic, or provide quick results without using excessive computing resources.
These firewalls work by verifying TCP (Transmission Control Protocol) connections. The TCP connection check ensures that the requested packet session is valid.
These firewalls work without using excessive computing resources, but they do not check the packet content. This means that if a packet contains malware but the TCP connection is intact, the packet will easily pass through.
Due to this weakness, circuit-level gateways alone are not enough to protect your company. Or they do a very good job.
Proxy Service Application Firewall
Proxy service firewalls use a proxy device (acting as a middle man) that inspects requests from external users at the application level. It inspects the contents of the request’s data packets and compares them with rules defined by the network administrator. Based on this inspection, the firewall allows or denies network access.
While the firewall allows access to external web pages, these firewalls can also hide the identities and IP addresses of internal users. This process can be a little time-consuming because it is very thorough.
But, it protects the information being affected and prevents external clients from connecting directly to the internal server.
Cloud Firewall
A cloud firewall is a security product that operates in the cloud and provides security by preventing unwanted access to private networks. Similar to older firewalls, cloud firewalls also filter network traffic.
That means; they allow data if secure, or deny data if not, but their difference is that they operate entirely in the cloud.
These firewalls are available as Software-as-a-Service (SaaS) subscriptions, and users can subscribe to their security.
They typically protect cloud-hosted online applications from unauthorized access and are used for security.
Stateful Inspection Firewall
A stateful inspection firewall is an advanced version of a circuit-level firewall that also verifies and tracks unwanted connections to provide more complete security.
These firewalls create a table that record:
- Source IP
- Destination IP
- Source Port
- Destination Port
Connections that cannot be verified are dropped, meaning they are not used, to prevent suspicious activity. The firewall then sorts connections based on established network-managed filters.
Additionally, the firewall creates its own rules based on its own rules, which filter the contents of data packets, thus providing security and accuracy. It can also monitor active TCP and UDP values.
Next-Generation Firewall (NGFW)
Next-Generation Firewalls (NGFWs) combine traditional firewall technologies with newer filtering functions, two types of which are Deep Packet Inspection (DPI) and Intrusion Prevention Systems (IPS).
Many NGFWs take older firewall functions, such as packet filtering or stateful inspection, and combine them with newer technologies. that means demanding both old and new.
The goal of newer technologies is to improve the filtering of network packets and make filtration more effective by incorporating more layers of the OSI model.
Network Address Translation (NAT) Firewall
A Network Address Translation (NAT) firewall matches a local private address with a public address to transfer information and keep the local network secure. It combines the two, allowing for a mix of private and local addresses.
Changing a device’s private address to the router’s public address allows the device to communicate with external networks. Along with, this also provides the network with a public location to send information.
Organizations that use multiple devices but require a single IP address use NAT firewalls to translate unique addresses to public addresses.
These types of firewall can block unwanted request or malicious data and prevent hackers from accessing the local network.
Firewall Placement: Where to Position Firewall
As firewall types have evolved, firewall placement options have also evolved. There are three most common firewall placements:
- Between internal and external networks
- Between external and DMZ (demilitarized zone) networks
- Between internal networks
Some networks require only a single firewall, but complex networks may require multiple firewalls.
For Example:
- Perimeter firewall – to protect against external networks
- Internal firewall – for packet inspection at Level 3
- Third firewall – to protect data at Layer 2
Limitations of Network Firewall
Here are the disadvantages of Network Firewall
Cost: The cost of a firewall depends on the type. Generally, hardware firewalls are more costly than software firewalls.
Restricts Users: Restricting users can get disadvantage for large organizations for their strict security mechanisms. This may prevent firewall employees from performing certain operations, even if they are necessary.
Issues with the Speed of the Network: Firewalls monitor every packet, so network operations may slow down or network speed may decrease.
Maintenance: Firewalls require continuous updates and maintenance with every change in networking technology. The constant development of new viruses poses a risk of system damage.
FAQs (Frequently Asked Questions)
What are The Different Types of Firewalls?
Packet-filtering, simple firewalls do work against rules for packets. Others are Next-generation, hardware, and software firewalls.
Which Types of Firewall is Best for Businesses Work?
Next-generation firewalls (NGFU) are ideal because they provide advanced feature threat detection or operate at an advanced level.
How is Hardware Firewall Different from The Software Firewalls?
Hardware firewalls protect entire networks, while software firewalls protect different pieces of software.
What is The Main Function of Packet Filtering Firewall?
It checks data packets against rules and decides whether traffic should be allowed or blocked.
Can I Use More Than One Type of Firewall?
Yes! Combining firewalls increases security through layered protection are provides.
Summing Up
Firewalls are important for your precious network security. Many types such as packet-filtering, stateful inspection, proxy, next-generation, and software & hardware firewalls provide different levels of safety.
You can protect your software from online threats. Each type has a unique purpose or performs a unique function: from allowing basic traffic to deep packet inspection.
Choosing the right type ensures you can effectively defend against cyber threats, protect systems and data from online danger, and maintain network performance.